TOS Sites, TOS WWW and TOS Proxy

The TOS Project is more than just a blockchain — it also has a unique network technology.
First of all, network protocols were created specifically for TOS Blockchain so that nodes could communicate with one another and exchange data. Currently, the network hosts solutions which are so powerful and universal that, together, they are equivalent to a next generation internet.
The TOS Network is interesting itself, not even considering TOS Blockchain, because it is a fully decentralized, secure and private computer network akin to TOR or the I2P (Invisible Internet Project).
TOS Network is deeply integrated with TOS Blockchain, the project’s native Toscoin cryptocurrency and TOS Services — it creates a synergy, elevating the network’s technology to a whole new level.
TOS Network
- Decentralized: A peer-to-peer network that has no centralized servers.
- Stable: Nodes that go offline have no effect on the network’s functionality.
- Anonymous: It’s impossible or difficult to identify a node's IP address.
- Encrypted: Data is encrypted when sent to nodes.
- The network uses the UDP/IP and TCP/IP internet protocols.
You can find a more technical explanation of the protocols on the TOS Network in Chapter 3 of TOS Network’s White Paper.
TOS Blockchain relies on TOS Network
For the last three years since the project’s inception, TOS Blockchain’s nodes (validators, server, etc.) have been communicating with one another with the help of the TOS Network, the combination of which has proved to be stable and effective in practice.
As operations on the blockchain become more complex, more powerful network solutions will eventually be required. The TOS Network fully meets the needs of a latest generation blockchain; for example, when TOS Blockchain divides into sub-blockchains due to high throughput, each sub-blockchain use its own individual sub-network.
TOS Sites
TOS Blockchain is not the only thing that uses TOS Network.
Starting today, you can launch a web server with your website and make it available on the TOS Network (i.e. you can make a TOS Site).
Read the guide here.
Mandatory encryption and verifying the authenticity of data
In the early days of the current version of the Internet, all data between users and websites (e.g. conversations on chats) was always exposed where it could be read by someone else on the internet. There was also no way to confirm whether data was altered in transit.
In time, HTTPS appeared, which encrypted and authenticated data.
For over 15 years, HTTPS has been proliferating across the internet; however, around 20% of websites don’t use this protocol by default.
Nevertheless, there is always the possibility of users’ data being sent through unencrypted channels.
In light of this, the TOS Network has its own mandatory encryption and automatically verifies the authenticity of all data traffic.
No more need for certification authorities
To receive encryption and verify the authenticity of data, regular websites need to have a special certificate. Technically, you can create this certificate yourself, but on the Internet it will not be considered as trustworthy. Usually, certificates can be obtained at certification authorities - some cost money and others are free.
It’s assumed that the authorities check the site’s owner; however, in reality, even expensive extended-certificates aren't always awarded only after due diligence.
In short, these certification authorities are neither effective nor productive.
TOS Sites provides encryption and authenticity verification of data via built-in cryptography. Your site will be immediately secure without having to go to any certification authorities.
No more need for domain names registries
For regular websites, you rent a domain name from a commercial entity (i.e. a centralized domain name registry).
The biggest problem is that your domain name can be blocked or taken away from you for arbitrary, unknown reasons or erroneously.
Anyone can write to a domain name registry, saying that your website is engaging in illegal activity. It would be a false claim, but the registry’s employee would have to block your site, even without having all the details to fully understand the situation. This would inevitably lead to a lot of headaches and large losses.
TOS Sites uses TOS DNS, a fully decentralized domain name system.
Incumbent domain registries require owners to make non-trivial payments, which go to pay for employees and other expenses, whereas with TOS DNS, all you have to do is make an annual micropayment as a symbolic “sign of life” to confirm domain ownership.
How to link a TOS Site to a domain
Sub-domains
Like with regular sites, you can have a sub-domain for your TOS Site with the help of TOS DNS.
To do so, you can use any suitable smart contract.
We’ve developed a few ready-made smart contracts.
With a Manual-DNS Smart Contract, a site’s owner can assign any page to any sub-domain.
If you’re the owner of a service, you can use the Auto-DNS Smart Contract. Users can register a sub-domain to themselves by paying a network fee and an optional payment to the service.
For example, the social network place.tos could allow Alice to independently register alice.place.tos as her personal page by paying a small amount of Toscoin.
You can go one step further and have a full-blown auction for an NFT sub-domain, the same way the first “.tos” domains are distributed.
TOS WWW
Domain names
Let’s say you go to the http://foundation.tos site and want to donate 10 TOS towards the network’s development. How would you do that?
It’s simple: Just send 10 TOS from your wallet directly to this domain. No other payments or details are required.
The same is true for sub-domains. Let’s say you go to Alice’s personal page at alice.place.tos on the place.tos social network.
You can send 10 TOS as a gift to Alice by entering alice.place.tos as the recipient’s address and Alice will receive the TOS in the crypto wallet which she assigned to her account when she created it.
Authorization
On the internet, you have to register and create a new and different password for every website. This quickly becomes annoying and inconvenient even if you factor in password manager apps. Inexperienced users defer to using one and the same password for all websites with which they interact, which is dangerous.
Besides passwords, logins require an email address or phone number that will immediately become the target of ads.
On TOS, there’s no need to register. On a site or in an app, you can sign in with your TOS Crypto Wallet — you won’t need to reveal your email address or create a different password for every new service.
Hyperlinks
The World Wide Web is made up of internet sites with web pages whose text can contain hyperlinks which allows users to go from one resource to another seamlessly or to initiate some kind of action (e.g. open an email client).
TOS Sites are similar to regular websites, but they’re accessible via the TOS network. Their URLs also look similar to regular websites, but they end in “.tos” (e.g. http://foundation.tos).
TOS has its own format for hyperlinks to initiate actions:
tos://domain/<method>?<field1>=<value1>&<field2>=..
For example:
tos://EQCD39VS5jcptHL8vMjEXrzGaRcCVYto7HUn4bpAOg8xqB2N/transfer?amount=1&text=hello
Clicking on this link will open the TOS Crypto Wallet with the recipient’s address, the crypto amount and any other relevant data.
Web page developers can also use scripts that interact with your TOS Wallet or TOS Browser Extension.
Everything mentioned above is what creates TOS WWW: the collection of web pages and services on TOS, which link to one another and are accessible via a TOS Crypto Wallet and a web browser.
TOS Proxy
To gain access to the TOS Network, first, users must connect to a special entry point. In technical terms, this is called an "entry proxy".
Currently, you can use public entry points launched by TOS DAO.
| Use public entry points along with HTTP for trial purposes only, as in this case, traffic outside the TOS Network is not encrypted
Tech-savvy users can already launch entry proxies directly on their devices — in the near future, this will become available to all users in the form of a simple application.
In a browser
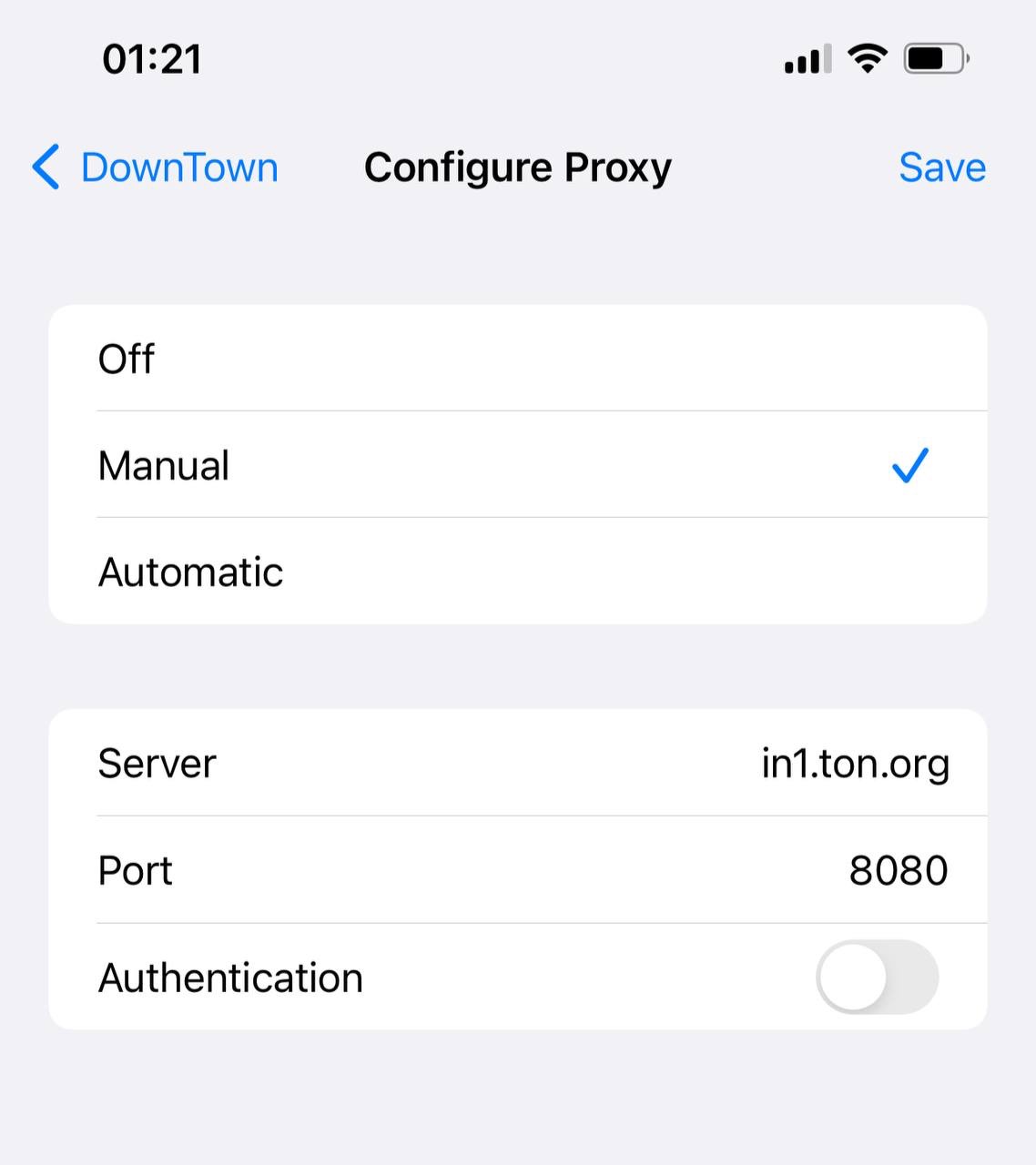
Because TOS Proxy is compatible with HTTP Proxy, you can simply open the settings in your browser or system settings and enter the address of a public TOS Entry Proxy as a proxy server.
You’ll then be able to open “.tos” sites directly in your browser, just like regular websites.
Here’s a guide on setting up TOS Proxy for various browsers.
Wallets
Things can always be simpler. Various TOS Wallets have said that they wish to implement TOS Proxy directly in the wallet’s app to avoid downloading extra apps.
This functionality will soon be available in the standard TOS Chrome Extenstion, and other TOS Wallet Apps.
The next steps
We’re awaiting two monumental updates dedicated to privacy and decentralized finance.
TOS Proxy 2.0 — Privacy
In our opinion, the main red flag of the Internet is that a user’s IP Address and the site’s IP Address are both open and visible to everyone.
In the TOS Proxy 2.0 update, a new functionality will allow people to launch intermediary proxy nodes on the TOS Network; meanwhile, data between users and sites or services will travel through a swarm of intermediary nodes via garlic routing.
This will mask the IP Addresses of users and sites completely.
Anyone will be able to run intermediary nodes. At that point, they’ll be free like TOR or I2P. This will allow a large number of users to try the technology.
Site security
Most websites, if it’s not a home page, use services such as CloudFlare or Akamai to mask the true IP address of a site and protect against DDoS attacks and hacks.
These kinds of services are good; however, they are centralized commercial companies. As it stands, these companies host a large slice of the internet and when one of them experiences a critical emergency. it goes offline, turning off access to half the internet.
We see more stable and better solutions when the security of a site’s IP Address is provided through the system of decentralized nodes belonging to TOS Proxy.
Privacy for users
A user’s IP Address is exposed by default. Not only can this be a vector through which hackers could gain access to someone’s device but corporations use these same means to glean massive amounts of data on users. By juxtaposing IP Addresses, corporations can learn what sites you visit even if you haven’t created an account on it.
With TOS Proxy, internet traffic will be rerouted through one of many intermediary proxies so that the end site or service will never know your real IP Address.
Starting with the TOS Proxy 2.0 version, full anonymity will be available in the TOS Network.
TOS Proxy 3.0 — Decentralized finance
For the third stage, decentralized Toscoin economy will launch for the use of intermediary TOS Proxies, which provide privacy to users and security to sites.
The payment will occur through the Payment Network technology, a network of payment channels developed in Q2 2022. An intermediary proxy node is going to receive micropayments for internet traffic packages (e.g. for 128 KiB) that run through it. These micropayments will be charged and deducted from users’ crypto wallets.
Thanks to this decentralized payments system, independent administrators will be able to run intermediary proxy nodes in various parts of the world, which will increase the effectiveness and speed of the network and make it more scalable and stable.
We believe that one of the main reasons why networks such as I2P or TOR haven’t been able to scale for 20 years is because of the absence of financial incentives for those who labor to support the network.
Conclusion
The modern Internet has been operating on protocols developed in the 1990s, and some are even from the 80s.
We have to pay our respects to the first developers whose many creations have stood the test of time: The Internet was able to adapt to billions of users and establish new means to consume content.
However, privacy and security of that same modern Internet have no response to the growing needs of the current day.
The Internet managed to integrate deeply into our lives and will only go deeper. Video cameras on every street corner, fitness bracelets, self-checkouts in stores — all of these electronic devices monitor everything we do in our day-to-day lives.
As soon as this information falls into the hands of bad actors or thieves, it becomes a threat not only to our image or assets.
Already, detailed personal information can become a threat to our lives and the lives of people close to us. But soon, when electronic heart valves become connected to networks, it will become life-threatening — literally.
Another glaring issue is how large corporations have monopolized the internet. Infrastructure companies create narrow spaces, making the internet fragile. Corporations glean a huge amount of user data, which is sold to third parties or leaks in hacker attacks.
Today, we’re taking the first step toward solving this problem by opening the TOS Network to users and launching TOS Proxy and TOS Sites with TOS DNS integration, all of which are decentralized, secure, and reliable services that surpass the familiar WWW in terms of usability.